The security of your systems and data, our priority
Configuration of your web services
If you want to host your own applications, you need to know that you must first hove a server on which to run these applications. Without considering the standard offers that give you access to managed servers with pre-installed required tools, you can also have your own server on your network or on the Internet (dedicated server or virtualized).
However, owning a web server is not enough to run your applications. You indeed then need install applicative servers such as the Apache2 web server and the database server MySQL.
To simplify the implementation of these vital services and possible associated tools, we offer our expertises. These cover the installation and configuration of Apache (PHP), Tomcat (Java) and MySQL as well as their security (see below). In addition to these basic configurations, we offer you tools and extended configurations that simplify the administration of your server (installation of tools such as PHPMyAdmin, SNORT and maintenance).
References
As part of our activities, we have performed such services for major French companies (including the installation and configuration) as well as small businesses (installation, configuration and maintenance).  Contact us for more information or to get a quote.
Contact us for more information or to get a quote.

Security of your web services
To ensure maximum security, we offer you not only the functional configuration of the servers (physical and software) but also the configuration of their security. This second configuration consists in several levels.
First, we propose the implementation of a security policy that aims at isolating the server applications, either by isolation at the process (a process by different user with limited privileges) or isolation software (chroot). Thus, each applicative server is seen as an independent entity. This lowers the risks of the propagation of an attack.
Second, we propose the implementation of a security policy on the server, including defining security policies on the inbound and outbound requests. This second configuration lowers the risk of an attack by blocking entry points of the server (ports) or limiting access to predefined addresses. To do this, we personalize iptables.
Third, we offer a "traffic monitoring" solution that allows you to get a daily report of the network traffic, simplified and clear. Thanks to this tool, we can offer you a real-time monitoring with automatic and instant alerts and real-time management of the critical ones.
References
As part of our activities and our partnerships (especially with the company YourOSoft), we have already offered such services.  Contact us for more information or to get a quote.
Contact us for more information or to get a quote.
Security of your web applications
Developing a secure application requires engineers to take into account security issues while designing the application. The development process then integrates all the required security processes to successfully implement and enforce the security policy.
In order to achieve an optimum level of quality, we can offer a complete analysis of your security needs: which need? Which security policy: DAC, RBAC? ... Based the formalization of this policy, we will then accompany you throught its implementation.
Regarding PHP solutions, we can also offer you an analysis of your solutions to validate the security of the information flows (internal flows, AJAX, .. ). Our methodology relies on in-house tools and open source tools like Spike, and PHPSecInfo PHPSecurityScanner.
References
As part of our activities, we for instance specified a security and control of redundancies policy for the synchronization of two data systems (MySQL and SyBase). This specification let us proposed a clear security policy which detects potential conflicts and allows bilateral synchronizations. This specification was followed by its implementation as well as the implementation of the synchronization module in its entirety, in Java.
If you would like more information about our solutions or ask for a quote, please  contact us.
contact us.

Security of your data
Adding security mecanism to your applications may sometimes, however, not be sufficient. Attacks may occur at other levels such as the physical level (destruction, theft) with direct attacks, or at the network and servers level (DDOS, ...). To ensure the security of your data, it is then also essential to ensure a daily automated backup of your data. This let you easily counter any attack (destruction, removal, compromise), but this also let you deal with other contingencies (hardware failure, network failure, ...).
To guarantee this level of safety and security, we implemented
- a tool which provides you with automatic and daily backups of your database
- an interface which allows you to easily recover those backups
- a tool which performs a daily reminder inviting you to download these backups
- a fully adapted interface and configurable
- a tool which performs incremental backups of your data (for example appendices directories for Drupal)
SSL Certificates
An important need
To ensure the security of your transactions (financial or not), the use of encryption technology is essential. We therefore propose the integration of SSL certificates for your hosting on our servers. These certificates allow you then to rely on HTTPS connections. We recommend our  our DigiCert partner, based on our partnership with the YourOSoft KFT company.
our DigiCert partner, based on our partnership with the YourOSoft KFT company.
If you already have an hosting solution, we propose to extend your exsiting offer with security features. First, we can manage all your certificates and their installation on your server (depending on the configurations of the latter). This prevents you from having to manage their storage or interact with nth intermediate. We will be your single contact! Second, as stated on the website of our partner DigiCert, several types of certificates exist. We can guide you to find the solutions that match your needs.
Which Security?
The SSL certificate solution that you need is strongly related to your situation. Depending on the desired level of security, trust to bring customers or even setup, you can choose between a Unified Extended Validation or wildcard certificate.
The Wildcard certificate allows you to use a single certificate for your entire domain. This has significant advantages for example if you use many subdomains. However, once one subdomain is corrupted, your wildcard certificate may also be compromised and thus your entire domain security.
The Unified Communications certificate allows you to use a signle certificate for up to three subdomains. Users are aware of this level of security, an icon "protected connection" such as 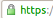 is available next to your address.
is available next to your address.
Finaly, the Extended Validation certificate allows you to use a certificate for up to three sub-domains and provides an optimum level of confidence for the users. Your safety is confirmed by the certificate provider and users are easily aware of it via the navigation bar in green in their browser 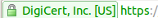 .
.
You do not know which certificate to choose? You do not know how to manage a certificate, or you want to delegate its administration?  Contact us!
Contact us!
 Digicert Wildcard certificate -
Digicert Wildcard certificate -  Digiciet Unified Communications certificate -
Digiciet Unified Communications certificate -  Digicert Extended Validation certificate
Digicert Extended Validation certificate


 Home
Home